Set up domain authentication to allow Axios HQ to send emails that look like they're coming from you!

Table of Contents:
- We will not take over your root domain
- Choose your sending domain
- Adding DNS records
- Internal DNS and anti-spoofing
- Send a test!
- What users can expect with a Custom Domain
- FAQ
- Common providers
1. We will not take over your root domain
We will never ask for DNS changes to be made on your root domain. Instead, your HQ communications will be sent from your HQ-specific subdomain.
- To verify and authenticate your domain, you will place our required DNS records on the account-specific subdomain of your choice (example: comms.your-domain.com)
Do not edit your domain’s primary DNS records: When adding Axios HQ’s DNS records, be sure you are not editing or deleting any records on your root domain. If you do, you may not be able to receive email.
This configuration protects the health and stability of your domain; if there are any spam complaints, bounces, blocks, or other reputation hits against your HQ sends, it will affect the HQ subdomain and our IP addresses, not yours.
- This also means that the DNS records we send over for your subdomain won’t impact your existing DNS records.
- Our SPF record will not count against any lookup limits and should not be added to any existing records.
- Our MX records will not disrupt incoming email to your email server. They exist to receive bounce and spam feedback.
Set up DMARC on your root domain: in your hosting provider, make sure you only include _dmarc as a subdomain on your root domain. You should not add it to any of your subdomains, as this policy should automatically apply to the new subdomain we are configuring.
We also recommend ensuring that your DMARC is set up to accept emails from subdomains by adding an adkim=r tag to your policy.
❗ Additionally, your DNS provider needs to support connecting your mailbox to a subdomain in order to properly set up this connection.
2. Choose your sending domain
Determine your send-from address
To begin setting up your custom domain, you will need to enter a unique subdomain and a domain you own.

The subdomain should be unique to HQ! Examples include:
- comms.your-domain.com
- info.your-domain.com
- axioshq.your-domain.com
The domain address should be whatever domain you intend to send from.
- This will be what follows the @ in your email address.
✅ When the above is complete, select “Generate DNS records.”
Choose a friendly subdomain! Your team may need to send from an address that includes the subdomain (ex: john@comms.your-domain.com.) This may be necessary depending on your spam rules and possible exceptions; we typically see this behavior with Outlook anti-spam policies.
3. Adding DNS records
To allow HQ to send on behalf of your domain, your team will need to add the five provided records to your DNS configuration.

🛠️ Once DNS records are generated:
- Navigate to “Settings” > “Custom Domain”
- Click the “TXT records” drop down to view records.
- Copy and paste these records into your DNS configuration.
- Repeat steps 2 and 3 for the MX records and CNAME record.
You will need these records to authenticate your domain:
- SPF record: This TXT record specifies Axios HQ as a valid email sender for your domain. SPF records are used to identify which IP addresses are authorized to send email on behalf of you.
- DKIM record: This TXT record allows Axios HQ to create an encrypted signature on emails sent on your behalf. DKIM signatures verify that the message that arrives at the inbox provider is legitimate, and actually came from the sender.
- CNAME record: The CNAME record is necessary for tracking link clicks and opens, and without one, links in your edition will not work. Ensure that these records are added to any internal configurations your team may have (like a VPN or LAN network).
You may see your links wrapped with something that looks very similar to your custom domain address. This is expected, and they will quickly redirect, all while tracking the link click.
These records are optional, but highly recommended:
- Our MX records exist to create a custom return-path using your subdomain, which will allow HQ to receive bounce and spam feedback. They are also recommended for any checks that your recipients' inboxes may attempt. If an email client looks for valid MX records and there are none, the message will almost certainly bounce.
MX records can be added retroactively. If your team decides to forgo MX records and sees unfavorable deliverability, these can always be added in at a later time.
Once all records are added to your DNS, click the “Verify DNS records” button in HQ. Each section should show “Verified” in green if properly added.
- DNS records can take up to 48 hours to propagate. Your domain will remain unverified until we are able to process that all three of the required records have the expected values.
- Note: your provider may automatically add your primary domain as a suffix to the hostname. In some cases, you may need to enter the entire record name (ex: comms.your-domain.com) while in others, you may only need to add the subdomain (ex: comms) as the host input.
If you do not see verified records, review your setup and hit verify again.
4. Internal DNS & anti-spoofing
This configuration allows Axios HQ to spoof your addresses, which your internal rules are built to block. Your team will likely need to make additional adjustments to any bulk rules or anti-spoof rules your team has in place. Learn more on our Allowlisting page.
❗ If your team has an internal DNS setup (ex: as part of a VPN or LAN network in your office/campus) add these DNS records to that configuration to ensure your HQ communications are accessible to your internal recipients.
- It’s especially important to add the CNAME record internally. Without it, your images may not display and links will throw an error for anyone on your internal network.
- This error may include messaging like "This site can't be reached" and will usually include the code DNS_PROBE_FINISHED_NXDOMAIN.
❗ If you have an anti-spoofing policy, please add your HQ-specific subdomain to the exceptions or bypass list to ensure that your editions are neither quarantined nor rejected.
- Go deeper: Find instructions for adding an exception to common anti-spoofing protection frameworks include Mimecast, Proofpoint, and Microsoft 365, here.
❗Some domains are highly sensitive and may require special permission to generate a TLS certificate. If you cannot generate a CNAME record and believe your domain is high-profile, you may need to have a representative from your organization reach out to our certificate vendor to facilitate the verification. Contact us at help@axioshq.com for more details.
5. Send a test!
Send a test edition from HQ, and include a link
Ensure that the DNS records have been properly implemented by creating and sending a test message to yourself! Include a link that you can click from your inbox. Make sure the link properly navigates you to its destination!
- Axios HQ will use the address you set in the “Reply-to” field in your Series Settings as the “Send-from” address, as long as it matches this domain. The Send-from address can optionally be specified.
- Click here to learn how to send a test.
Seeing blocked images or EXTERNAL warnings? Review our allowlisting recommendations.
6. What users can expect with a Custom Domain

With a Custom Domain in place, users within Axios HQ can set the send-from address for any series to any email address that includes your root domain!

In the above example, we see Pepper Potts (of Stark Industries) sending a message from Axios HQ on behalf of Tony Stark.
- Pepper set the send-from address to Tony's email, so it looks like the message is sending from Tony.
- Pepper kept herself as the "reply-to" address, meaning any responses will go to her inbox.
- Because Tony's address is a real address within stark-industries.com, his profile picture is displayed.
- The selected subdomain in this example is axioshq. It is only visible within the mailed-by and signed-by fields.
The send-from address does not need to be an active inbox. The send-from address can be set as any address as long as it matches the root domain.
We do recommend that the reply-to address has an active inbox. The reply-to address should be set up to receive responses from your recipients.
You can also send-from an address that includes the subdomain.
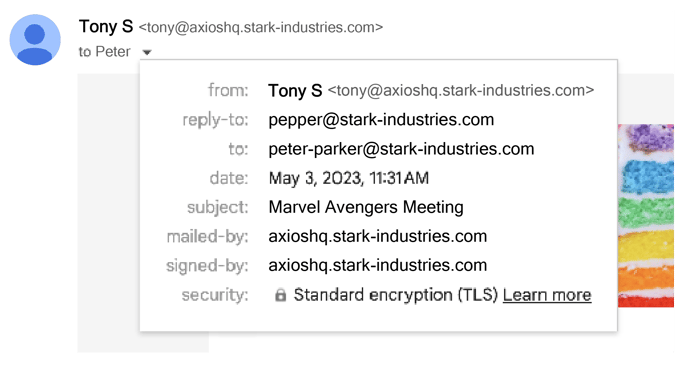
You may choose to include the subdomain if that fits your branding guidelines or your allowlisting requirements.
- Pepper has set the send-from address to one that looks like Tony's email, but it is not exact. Because Tony's address includes the subdomain, it is not a real address within stark-industries.com.
- As noted above, the send-from address does not need to be an active inbox. This means any send-from addresses that include the subdomain will be considered properly configured without additional IT lift.
- Because "tony@axioshq.stark-industries.com" is not an exact match to Tony's true address (tony@stark-industries.com,) it will not display his profile picture.
Including the subdomain in the send-from address is particularly relevant for organizations that use Outlook. Review our Outlook allowlisting recommendations here. You can find specifications about the Custom Domain setup at the bottom of that article, here.
7. FAQ
📫 Sending
Can I still send from HQ before we set up a custom domain?
Yes, you can still send from HQ without a custom domain. Your email will come from noreply@axioshq.com and any replies will return to whatever address you set as your reply-to email.
My custom domain is set up, but none of my messages are coming to my inbox.
Adding a custom domain can flag anti-spoof policies your team has set up. If it seems like your messages aren't sending, check out our allowlisting documentation for recommendations on setting up rules, exceptions, and quarantine bypasses that will allow your messages to reach your internal recipients.
My custom domain is set up, but images are blocked / there's an EXTERNAL warning banner.
Review our allowlisting recommendations here.
Can I use multiple custom domains with one HQ organization?
At this time, we do not support more than one custom domain per HQ organization.
What email address can we put in the send-from field?
Any email address that matches your domain! This address does not even need to be an active inbox. We do recommend that the reply-to address is active to receive responses.
📫 DNS Configuration
When troubleshooting your DNS configuration, we recommend first hitting "Verify DNS records" on the Custom Domain page to ensure that all of your records are properly authenticated.
My DNS records are not verifying.
Navigate to "Settings" > "Custom Domain" and ensure that the provided value and the current value match for the SPF, DKIM, and CNAME records. Check for any typos.
-
SPF: If your SPF record is not verifying, make sure it has not been included as part of an existing SPF record. Our SPF records should not live on your root domain, and will only verify if they are on the subdomain you've configured for HQ.
-
DKIM: Typical DKIM mismatches are due to typos and misspellings. Remember, the DKIM record is unique to each setup!
-
CNAME: Ensure that this record is added to both your internal and external setups. This record will properly verify if added to your external setup, but will need to exist on your internal setup to resolve links on all networks.
-
MX: MX records are technically optional. We typically see mismatches when the priority is accidentally included in the value. Check the Current Value field in HQ to ensure there are no typos in this record.
My records say None found.
None found indicates that the hostname cannot be found or is improperly entered in your DNS configuration.
- Some DNS providers automatically add the root domain as a suffix to the hostname, in which case you can remove it from your inputs. You may not need to enter the entire record name (e.g., comms.your-domain.com) and instead may only need to add the subdomain (e.g., comms) as the host input.
My CNAME record will not verify.
Some high-profile domains are unable to generate a TLS certificate without explicit permission. If your CNAME record is not verifying and you believe you have a high-profile domain, you may need to have a representative from your organization reach out to our certificate vendor to facilitate the verification. Contact us at help@axioshq.com for more details.
Can we use a hard fail instead of a soft fail for our SPF record?
Yes! This can be adjusted as you see fit.
Can we change the include:mailgun to something more specific?
Yes. include:mailgun is necessary for verification, but once your records are verified, you can remove it and add a more specific record; simply replaceinclude:mailgun with the value you would prefer.
Can we use multi-level subdomains?
Yes, but ensure that only your root domain goes in the "Domain address" field. Any multi-level or nested subdomains should all be included in the subdomain field.
8. Common providers
Below is a list of common DNS providers and instructions on how to add the appropriate DNS records.
- AWS:
- AWS does not allow you to set multiple MX records per hostname. To circumvent this issue, add a single record that has both MX values on separate lines.

- AWS does not allow you to set multiple MX records per hostname. To circumvent this issue, add a single record that has both MX values on separate lines.
- Cloudflare:
- Cloudflare offers a setting to dynamically flatten the CNAME records to the A record of the root domain. Although the record is functional, it is not accessible to our ESP and will likely prevent an https certificate from generating.
- The CNAME record must be set to "DNS only" and not "Proxied" in order to verify.

- GoDaddy
- This provider automatically includes the root domain for any DNS records, so please be sure to only add the subdomain for your Axios HQ additions.
- Google
- Check if you have the correct credentials to set up your DNS configuration by navigating to google.domains.
- This provider automatically includes the root domain for any DNS records, so please be sure to only add the subdomain for your Axios HQ additions.
- Google may reject adding two separate MX records for the subdomain. To address this issue, enter one record with the value
10 mxa.mailgun.organd then click "Add to this record" to add another entry for it. Then you will enter10 mxb.mailgun.org.
- Valimail
- If you use Valimail for DMARC monitoring and enforcement, your SPF record may appear with additional characters, likely due to Valimail's use of macros. Our ESP is not able to verify SPF records entered into Valimail. We recommend hosting the SPF record via another DNS provider to be able to verify the domain.
- Verio
- Does not support adding TXT records to subdomains, and for that reason we are unable to integrate a custom domain with this provider.
- Wix
- Wix does not support adding MX records (optional) to subdomains.
- WANworX
- This provider requires adding the subdomain as a new domain in WANworX and adding the DNS records we provide to the new domain.
- MX records may need to be altered in order to enter them. You may also have to enter each MX record as both an MX and CNAME record.
- MX (hostname: axioshq.your-domain.com) (priority: 10): mxa.mailgun.org
- MX (hostname: axioshq1.your-domain.com) (priority: 20): mxb.mailgun.org







