Secure your user logins with Single-Sign On (SSO)

SSO is an authentication that allows a user — someone who will write, edit, or send your series — to log in using just their email address and the click of a button. No password necessary! Implementing this integration allows for an easy sign on experience for employees with particular credentials, and provides security when off-boarding those you no longer wish to have access.
⭐ SSO requires an upgrade from the Essential Package.
Why it matters: Security is important, and manually updating large lists of employees can be cumbersome. Requiring a login via SSO ensures that only employees with active company email addresses have access to Axios HQ.
🔍 How it works: Owners and admins can access SSO by by navigating to “Settings” > “Integrations”.
Table of Contents:
- Identify who has access to Axios HQ
- Providers we support
- Connecting SSO
- Step 1: Verify your domain
- Step 2: Connect your SSO provider
- Customizing your connection
- Signing in to Axios HQ
- FAQ
- Common providers
1. Identify who has access to Axios HQ
Identify who on your team should have access to Axios HQ. We recommend provisioning an All Staff list in order to streamline the setup process.
- If you prefer a specific user pool, create a list of users who will be writing, editing, or sending series via HQ.
2. Providers we support
We partner with WorkOS to facilitate most of our integrations. You can find an introduction to WorkOS and their workflow here.
Identity providers we support:
| AD FS SAML | Duo SAML | miniOrange SAML | React Native Expo |
| ADP OIDC | Firebase | NetIQ | Rippling SAML |
| Apple OAuth | Generic SAML | Okta SAML | Salesforce |
| Auth0 SAML | Google OAuth | OneLogin SAML | Shibboleth Generic SAML |
| Azure (Entra) SAML | Google SAML | OpenID Connect | Shibboleth Unsolicited SAML |
| CAS SAML | JumpCloud SAML | Oracle SAML | SimpleSAMLphp |
| ClassLink SAML | Keycloak SAML | PingFederate SAML | VMWare SAML |
| Cloudflare SAML | LastPass | PingOne SAML | |
| CyberArk SAML | Microsoft OAuth |
When you are ready to set up Single Sign-on, you will follow instructions through the portal provided in the platform. Details for this workflow are found below.
If you'd like to review the steps you will be taking, check out the instructions for your specific provider here.
3. Connecting SSO
🛠️ How it works:
- Navigate to "Settings" > "Integrations"
- Locate "Single Sign-on," and click "Connect."
💡 Only org Owners and Admins have access to the "Integrations" page.
If this view is not available to you, please request that an Owner or Admin in your organization adjust your permissions.
4. Step 1: Verify your domain
🛠️ How it works
- In the Single sign-on setup modal, click "Add domain(s)."
- Enter the domain you would like to verify, (this should be the email domain your users will be logging in from,) then click "Continue."
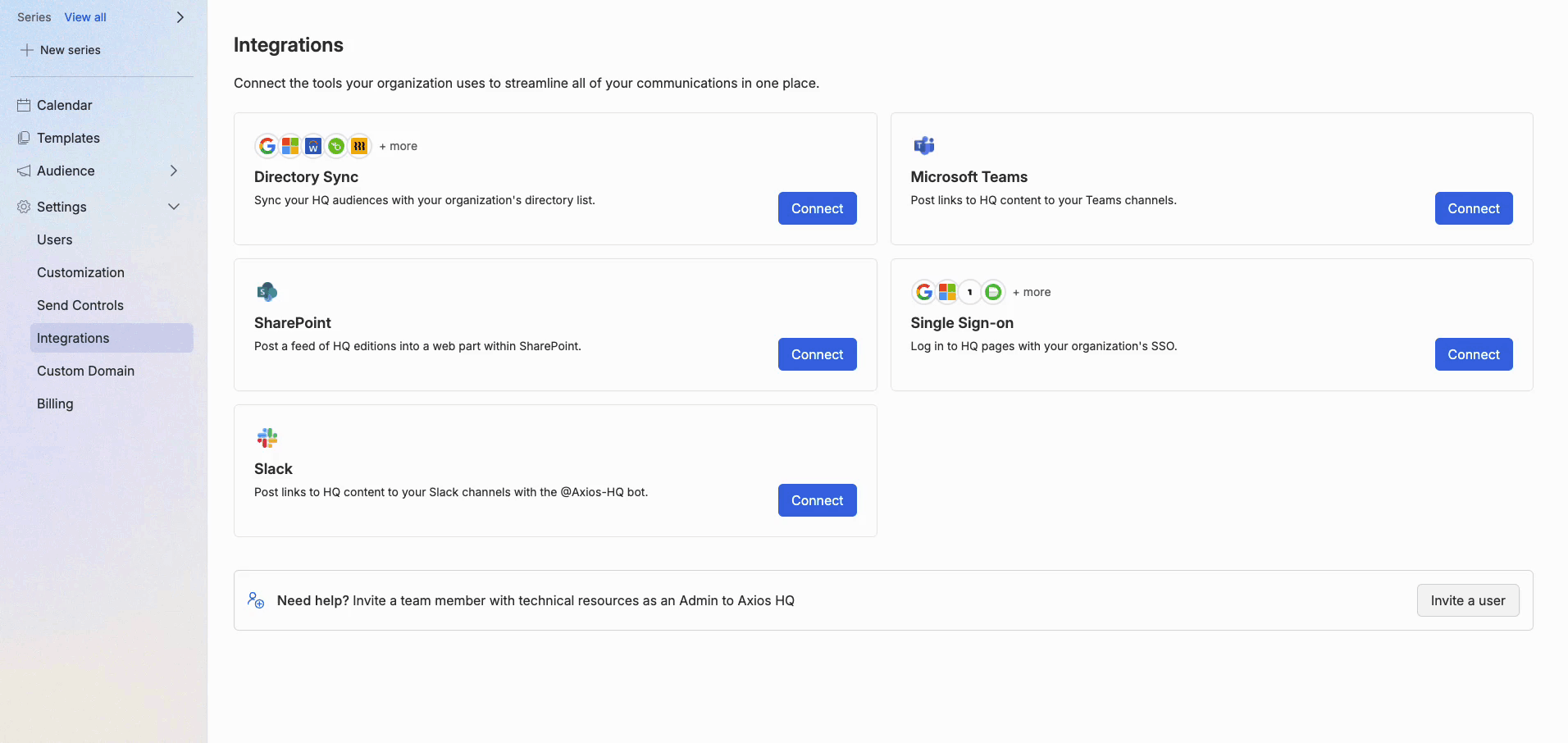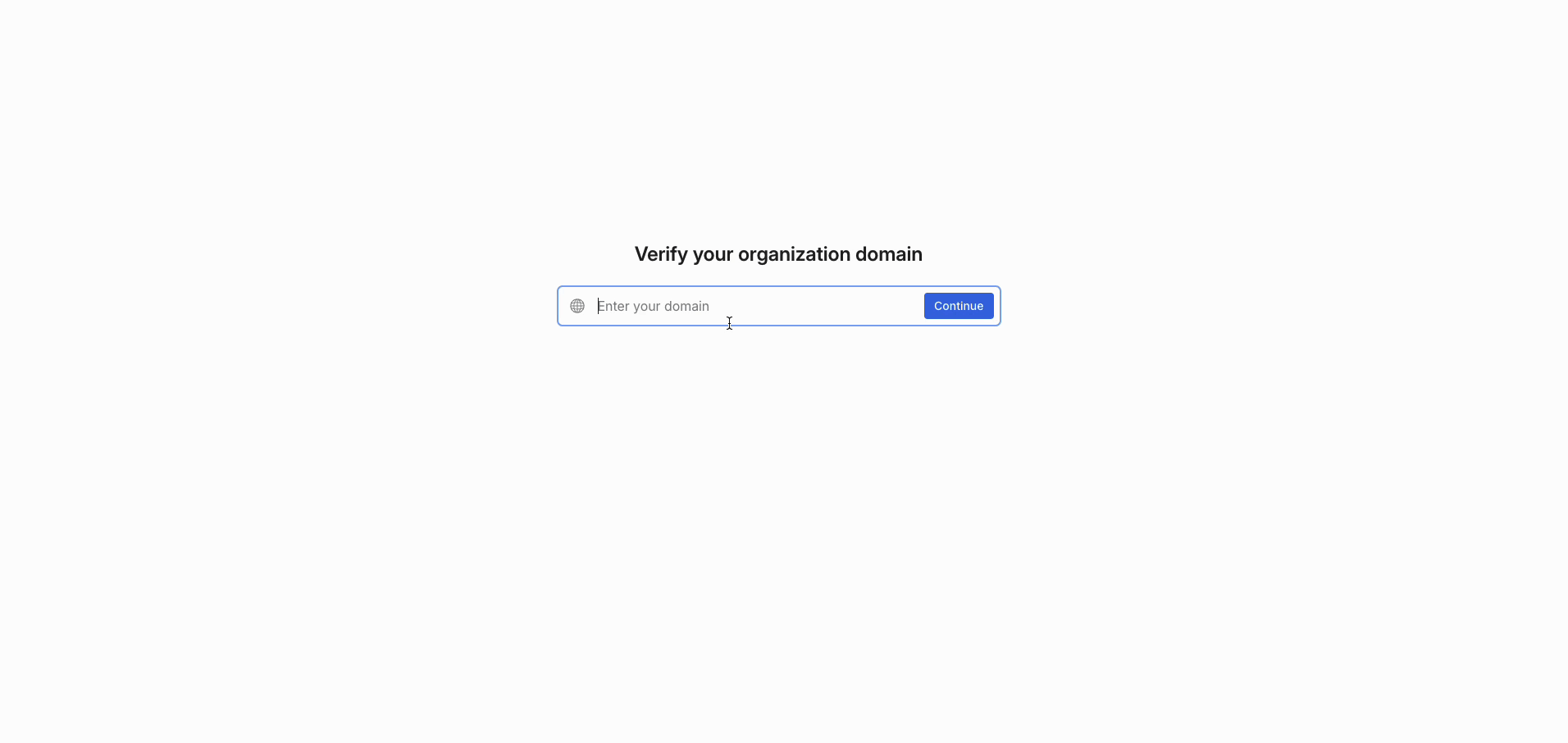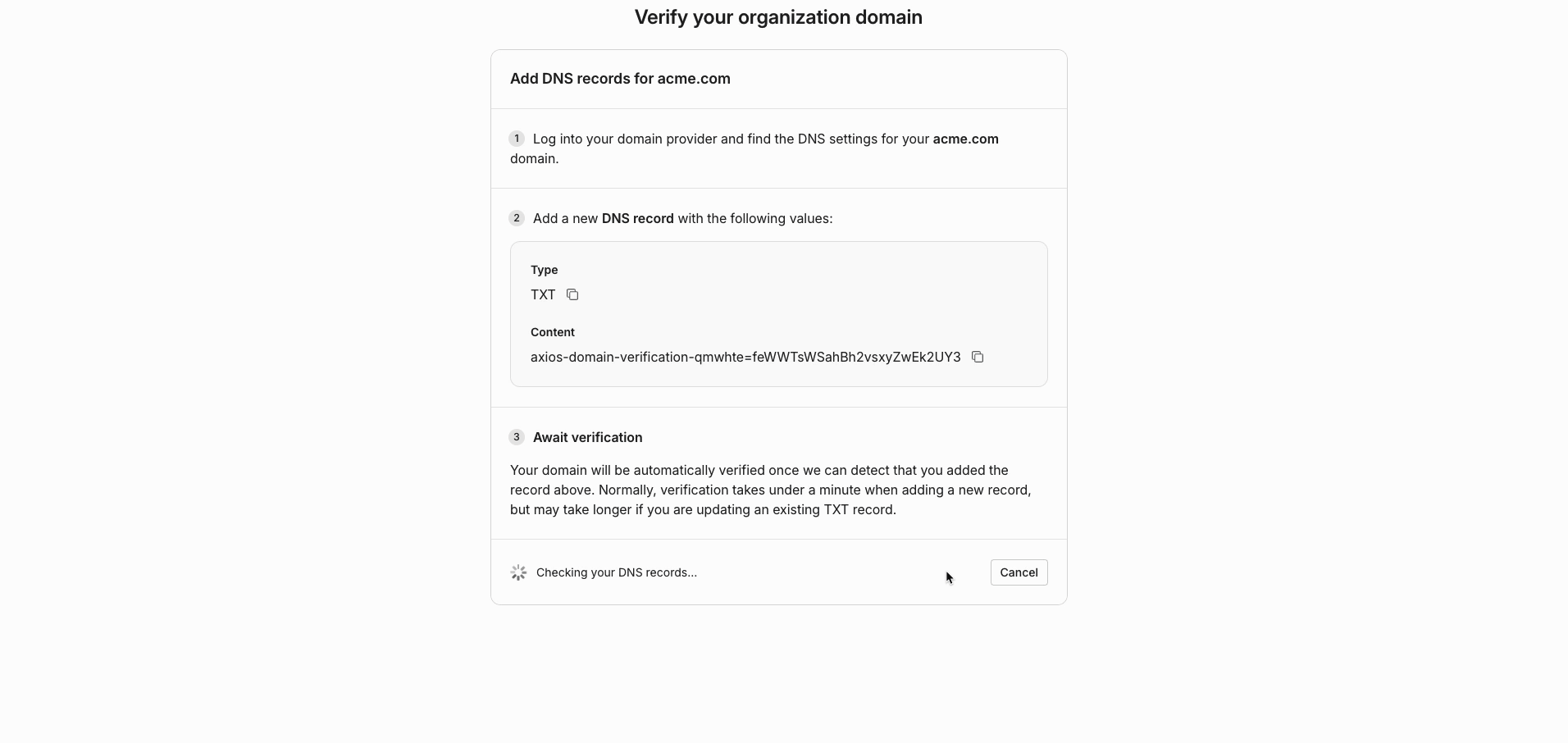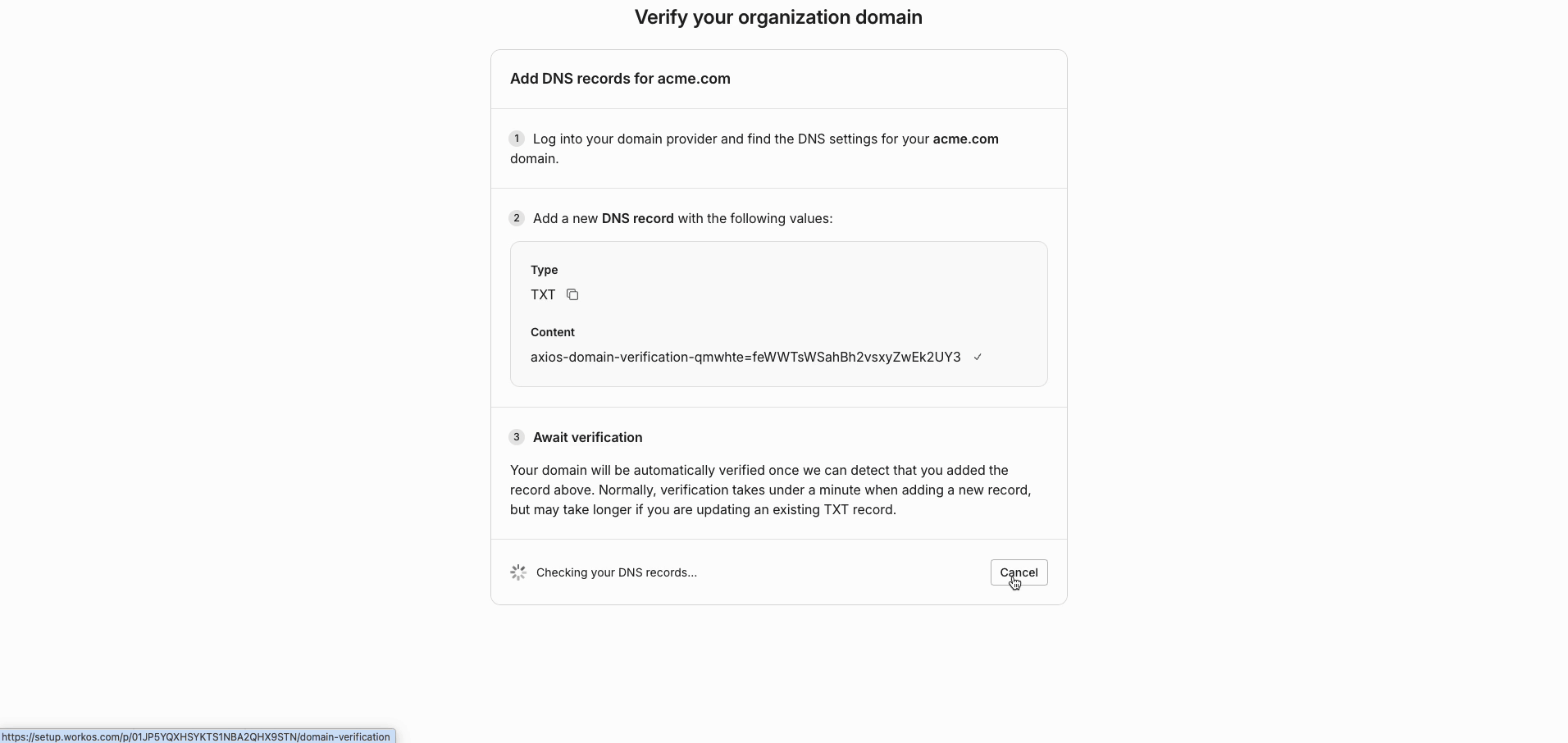
- Add the provided record to your DNS configuration.
- Once your domain is verified, click "Resume setup" to continue the SSO setup.
This domain verification is a security step that ensures that your organization can authorize this domain for SSO access. It prevents a potential bad actor from authorizing a domain that they do not own.
You can remove this TXT record once the domain is verified.
The entire record must be added to your DNS configuration, including the preceding "verification_token=" portion. Use the "Copy" button available next to the provided Content in order to ensure you are properly adding the record to your DNS configuration.
💡 When at least one domain is verified, you will see the view below. 
✍️ Interested in adding more domains? Click "Add domains" to add each additional domain you would like to verify for SSO.
5. Step 2: Connect your SSO provider
 🛠️ How it works:
🛠️ How it works:
- Click "Connect Integration" to continue to the SSO setup portal. (You will be taken to a setup portal provided by our vendor, WorkOS).
- Select your identity provider and walk through their setup instructions.
- Setup instructions will vary by provider.
- Once the SSO setup is complete, you will see the linked connection as a row in the Integrations table in HQ.
- You will be able to view and modify this connection by selecting the gear icon.
Remember, the way you configure your user groups within your SSO provider will determine who has access to the Axios HQ platform. If a user cannot log in with SSO, please check to ensure that they are correctly provisioned in these groups.
- We recommend setting up automatic provisioning, or connecting an All-Staff group within your identity provider, for your convenience.
6. Customizing your connection
Once your SSO connection is in place, you’ll have the ability to configure additional settings for this integration.
- SSO Optional and Required
- SSO Optional (our default setting): Allows users to sign in with either a password or SSO
- SSO Required: Allows users to sign in using only SSO
- Just-in-Time (JIT)/ Automatic provisioning
- Without auto-provisioning, users will need to manually invite each new user to Axios HQ before they can log in (this is our default setting).
- When auto-provisioning is on, your HQ workspace is open to anyone designated within your SSO provider. As long as these individuals are provisioned for SSO, they will be able to log into Axios HQ on their own as a new user with default Member permissions.
- With auto-provisioning turned on, an account will automatically generate for new users logging in with SSO, if one does not already exist for them.
To enable either of these settings, please reach out to help@axioshq.com.
7. Signing in to Axios HQ
With JIT/automatic provisioning turned off, your team will still need to be added to the HQ platform by an existing user.
- Invite additional users by selecting “Add user” on your Organization page, or adding a collaborator to a particular newsletter in that newsletter's Settings. Anyone within the organization can invite new members.
👉 Navigate to our login page and select "Log in with SSO". Then, enter your email address and click "Connect".

- Whoever you provision in the first step is who will have access to log into the platform. If you try to add a new user who has not been provisioned and you are set to SSO: Required, that user will not be able to access anything in Axios HQ.
- Being unable to sign in can be frustrating for users, and often results in a support ticket with HQ and ultimately your IT team.
- Remove the possibility of interruption by provisioning an All Staff list instead. Users still need to be invited to collaborate on a newsletter, so you will have control over who has access to the platform based on their HQ credentials.
8. FAQ
🔒Login & Logout
What can I do if users are seeing an Axios HQ error message when trying to log into the platform?
Please ensure that an account has been created for the user on our platform, then ask them to try logging in via SSO again. Without JIT provisioning enabled, an HQ account must be manually created for each user.
Users are seeing an error with no Axios HQ branding when logging in. What can I do about this?
Error messages that do not include Axios HQ branding indicate an issue related to the setup within the identity provider. Please ensure that the user has been provisioned for SSO for this connection to resolve this.
Does Axios HQ redirect a user’s browser to the IdP to terminate the session when a user signs out?
No. Axios HQ does not redirect a user’s web browser to the IdP to terminate the session when a user signs out.
🔒 Setup
Does Axios HQ support automatic de-provisioning/removal of users?
No. At the moment, Axios HQ does not support automatic de-provisioning of users; however, with SSO set to "required", users who have been removed from the SSO user pool within your identity provider will not be able to log into our platform.
How do I generate a new new X.509 Certificate?
You should be able to navigate to the section where the certificate was initially generated within the IdP application to generate a new certificate.
What federation standards does Axios HQ support?
Axios HQ (via WorkOS) supports SAML 2.0 and OpenID connect (OIDC).
Does Axios HQ support IdP-initiated and/or SP-initiated SSO connections?
Axios HQ (via WorkOS) supports both IdP-initiated and SP-initiated SSO connections.
For SP-initiated SSO connections, does Axios HQ include the Assertion Consumer Service URL in the SAML request?
Yes. Axios HQ (via WorkOS) includes the AssertionConsumerServiceURL in the SAML requests.
What attributes are required for this SSO connection?
The required attributes for SSO are id, email, firstName, and lastName. These attributes must be in a string format.
Does Axios HQ have a "break-glass" or "back door" Admin account?
Axios HQ does not have an account that can subvert the SSO: Required setting. If you need to circumnavigate SSO requirements to access Axios HQ, please have an Admin or Owner reach out to help@axioshq.com. We can toggle the requirement off to allow access via password.
9. Common providers
Entra ID / Azure & Okta
-
If you're using either of these providers for both SSO and Directory Sync, we recommend you create two separate Enterprise Applications for Axios HQ in order to separate these member pools.
OneLogin
- You may want to make use of OneLogin’s SAML Custom Connector, which enables you to launch HQ from your OneLogin dashboard, bypassing the SSO login screen on HQ.
- If you run into an issue related to the login bypass not occurring (getting redirected back to the login screen), please change the SAML Initiator to OneLogin (not Service Provider) in your OneLogin settings.
WorkOS' documentation on OneLogin may be a helpful troubleshooting reference.







